
For cyber security folks, we’re both horrified and laughing that a company named “Change Healthcare” who has stockpiles of marketing jargon for “Improving IT Security” also made the news for a cyber incident.
As a cyber security professional by day and a partial owner and investor of a new medical business, this breach hits home deep.
HealthCare’s Commitment to Cyber is … Comical.
304 hits for IT Security on http://www.changehealthcare.com

Data Security Shouldn’t be a High Stake Gamble…
http://www.changehealthcare.com

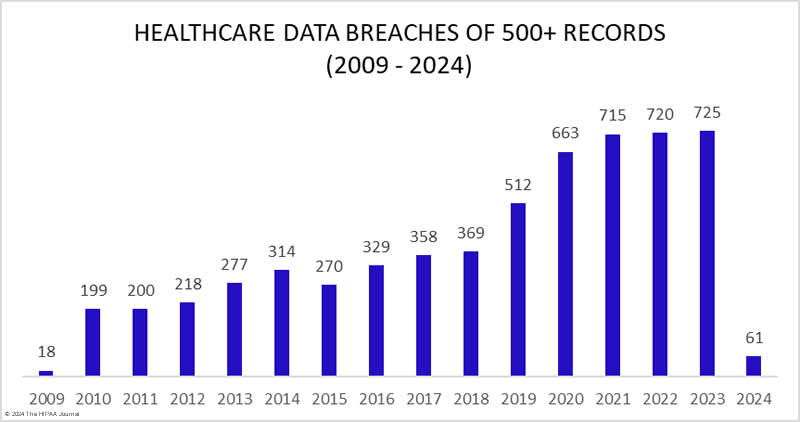
Attacks in HealthCare Are On The Rise
In 2023, the healthcare sector saw 725 data breaches reported to the Office for Civil Rights, marking a record year for both the number of breaches and the volume of records compromised, with over 133 million records exposed. This trend represents a significant increase in data breaches within the healthcare sector over the years, underscoring the growing challenge of protecting patient data against cyberattacks and unauthorized disclosures. For detailed statistics and trends on healthcare data breaches, you can visit HIPAA Journal’s website on healthcare data breach statistics.
History Repeats Itself, Health Exchange Optum Health have been here before.
The Optum Health subsidiary of UnitedHealth Group since 2011, previously experienced a data security incident, shedding light on the vulnerabilities even large healthcare entities face in the digital age. OptumRx, a branch of Optum, reported a vendor privacy incident impacting personal information of specific state residents due to a vulnerability in the MOVEit Transfer software. This incident, occurring between May 30 and May 31, 2023, allowed an unauthorized actor to access and obtain sensitive data, although financial details like Social Security numbers or driver’s license information were not involved. OptumRx has since committed to notifying affected individuals and offering complimentary credit monitoring and identity protection services through Experian for two years.
In a separate but related event, UnitedHealthcare Services Inc. filed a notice of data breach after discovering unauthorized access to an email account of Equality Health, an Accountable Care Organization working with some UHC members. This breach compromised sensitive information including names, dates of birth, genders, addresses, Social Security numbers, UHC member ID numbers, and more. The breach, resulting from an employee error and previous mistakes, prompted UnitedHealthcare to send data breach notification letters to affected individuals, advising vigilance against fraud or identity theft.
And the recent cybersecurity incident involves Change Healthcare, a subsidiary of UnitedHealth Group, which experienced unauthorized access to parts of its IT network. While the full impact of this breach is still under investigation, it underscores the growing challenge of protecting patient data within interconnected healthcare systems.
An insider view to healthcare cyber security
It’s easy to make jokes or regurgitate history news articles with ChatGPT…but as someone who is a both cyber security worker in my day job and a small investor in a medical business, I’ve began to learn some really concerning things about the healthcare industry.
- Security Updates = Bad, medical device software companies depend on a select few software driver providers. These driver company are not “tech” companies and the dev cycles move slow. So when you update your computers with the brand new security software then you x-rays stop working, your charting software stops working and all those handheld medical devices can’t integrate to the medical software anymore … revert back and never update again!!!
- IT Support, Disable All Security Things!, because the support teams for these medical device companies continue to blame “security”. I can’t tell you how many times medical device support staff asked me to “Disable My Firewall
“Disable Windows AV” or remove my GPOs without understanding what their .NET or C++ application is actually doing. - IT Support, Give Me Admin Plz – Yes again, because I can’t explain how many times people say “just install this remote management software” so I can take control over your system as System Administrator … Just say No
- No authentication, No Problem, we still live in this world, interoperability between various vendor medical devices is hard, so many times they use a standard protocol and driver that is open and unauthenticated … feels like we’ve been here before?
- Send and Open All the Files! – Some companies have modern digital ways to send files, other providers are small and still use email and fax. At scale, this creates a world ripe with potentially malicious files being shared between parties and often an immediate need to open them … ripe for phishing campaigns …
And I’m afraid to even dive into the security posture of emerging Cloud SaaS software. As someone who has done a few security assessments of SaaS medical software, it continues to amaze me how many sales people will get on a call to pick a fight with the cyber security people.
Almost like, “How dare you insinuate our product is insecure” because we got a certification and an audit report! No surprise… that the cyber security conversation is either omitted or saved for later after the sales pitch already went to management.
But alas, now we simply move our problems from our computers to someone else’s computer in the cloud. Where a stolen username/password can be used to steal not just one medical office files but thousands of medical office files over the wide open internet.
In theory, centralizing data management and cyber security might be better than managing a bunch of small and medium companies without trained cyber security IT. However, I find history repeats itself. Only this time, with even more eggs in one basket that you don’t control.
Who’s Fault Is it?
It’s Complicated. There’s reasonable reasons why all these security gaps happen. Sometimes these issues become inherent and accepted risks.
I mean, if you need to view an xray to provide medical care then the system needs to take priority and always work. No wonder why doctors prioritize patient medical care before a theoretical data breach.
And business needs to run and make money, if they don’t then they cannot pay staff and ultimately physicians cannot help people get healthy.
And your small town rural medical office won’t have the same bells and technology whistles because it might not be affordable or accessible. And aging patient pools may not familiar with the latest technology for sending files. You add this reality up, and you have insecure devices, insecure software and random files being moved around the world.
But …. we’re not talking about small mom and pop shops being breached
We’re talking about a large multi billion dollar company. These companies are stewards of our data and our medical health. These companies, often create oligopolies that give the patient and the small medical companies little choice but to use their solution. Even today, my medical software company only supports one insurance broker. Change Healthcare. And I had no real choice in the matter to either get paid quickly or manually file paper claims which are also insecure and take months, not weeks to process.
So for many us in the medical industry, this type of cyber news cycle becomes an accepted risk. We seem cursed to repeat our behavior over and over again while innocent people suffer.
cyber attack like this hurt more people than just the big corporations
Here are the after effects. If sick people have a hard a time getting their prescriptions processed then they may suffer critical heart attacks or stroke.
Small medical businesses cannot pay their employees if they cannot collect their insurance claim payments. Small businesses with low funds may even bankrupt because they can’t be paid within a month or two. All of this pain and suffering, only benefiting big corporate hospital chains and dental office who can weather the storm.
So I think of the patients who will suffer without their medicine and the small medical office workers, I think of their office staff and their medical assistants making just enough money to get by.
I think of innocent people working a noble and ethical job just helping others and exposing themselves to covid and sickness everyday for a few dollars a month. That doesn’t even begin to scratch the surface of the pain of the people who will suffer from identity fraud, phishing campaigns or additional embarrassment if their data has been stolen or leaked.
All that because of security attacks on a software company that most regular folks had little choice in choosing.
What Can we Do, MORE OF THE SAME
- Use Multi Factor Authentication on all you accounts
- Push your vendors to provide regular updates and patches
- Don’t install remote management software, let the vendor “Instruct Your IT staff” not “Control” your system
- Don’t give “Admin” access to regular business users …
- Don’t “disable the security stuff” just because, and if you do start with a a test system and if it doesn’t work, then re-enable it again
- Test patches on a “test” system with all the medical software and gadgets before rolling it out to every system, avoid the panic and surprises that often causes fear from change
- Run advanced host endpoint detection response (EDR), antivirus and antimalware don’t cut it anymore
- Run email security software such and Microsoft Defender for email or Area51, scan and quarantine threats. Yes you will be “missing” a few emails from time to time …
- Create encrypted backups of your critical data, limit access who can delete and overwrite those backups
Technology has come along way. Advancements in Microsoft’s security product line has made securing small and medium size businesses even more manageable. Everything from email security with built AI threat detection, to endpoint security detections, to mobile device management, hello for business and TPM encrypted biometrics and data loss prevention and auto data discovery and labeling. And even with all that, hackers gonna hack.
But it will never get better, unless we all do what needs to be done…
IT’S LITERALLY IN THE NAME
CHANGE HEALTHCARE
cybersecurity
